Call today for a Red Team threat assessment: (332) 208-5900
Services For Cyber Risk Management
Expert services to address specific security needs within your organization.
Tagmata Services
Experienced Approach to Protecting Critical Information

Emerging Cybersecurity Landscape
Every risk is unique and every infrastructure is different
As threats to information security continue to evolve rapidly, and stakes become higher, hostile actors are incorporating attacks that not only target traditional critical information nodes but also look at unprotected individuals and infrastructure as potential entry points of access to the desired information. Current Cyber defense products and models do not incorporate or consider alternative cyber and physical attack vectors.
As your company becomes technologically more dependent on the IT innovation economy, protecting critical information is paramount to reducing your risk and increasing your opportunity for cybersecurity success.
Cyber, information, and physical Security protocols are tested and proactive in their approach:
- Risk Assessment and GRC
- Vulnerability Assessment
- Cloud intelligence
- RedTeam Operations
- Tagmata AI Tools
Information Security & Cyber Risk Management Assessment (ISCR)
Respond and react quickly to minimize your brands impact in a cyber event
The Program is designed to evaluate and provide an assessment for options to protect your brand by securing sensitive and critical digital processes where data is collected and used by the business, validating compliance with various control requirements.
Tagmata will assess the control requirements which will be derived from internal and external governance factors and make “high-level” suggestions based upon these Internal factors for potential security framework, such as NIST or ISO while also providing some recommendations on External factors such as General Data Protection Regulation (“GDPR”) and Payment Card Industry Data Security Standards (“PCI-DSS”).
Tagmata Crisis Management/Incident Response programs are customized and include:
- Focus is on Brand Protection
- Define Cyber Risk Management
- Preparing to Respond
- Cyber Crisis Management Structure
- Framework for Decisions & Execution


Security Consultation
Provides Security Experts to Support Strategy, Compliance, Technical Architecture and Operations
Professional security consultants can be the solution to the dilemma of not having enough knowledge and expertise to handle the latest cyber attacks, threats, and vulnerabilities.
Our Security Consulting Services offers the expertise and proven recommendations to help you enhance your IT security posture, reduce your information security risk, facilitate compliance, and improve your operational efficiency. Our Security Consulting Services offers the expertise and proven recommendations to help you enhance your IT security posture, reduce your information security risk, facilitate compliance, and improve your operational efficiency. We can deliver a wide range of capabilities – from penetration testing to regulatory and standards compliance, to vulnerability and risk assessments, PCI DSS, GDPR, and forensic analysis.
We can deliver a wide range of capabilities to support your risk and security challenges.
Types of Security Consultants:
- Risk Assessment and GAP Analysis
- Regulatory and Standards Compliance
- PCI DSS & GDRP
- Strategy, Architecture & SecOps
- Forensic Analysis
Security Assessments
Provides Security Experts to Support Architecture and Operations
Security assessment begins through the identification of all critical technical assets and processes within the organization. These include physical assets, such as servers, routers, and information on network services, remote access locations, what information travels over the network, who, what and when data can be accessed. Next, well quantify their importance by placing a value on the assets along with risk priority. Tagmata works diligently to involve business owners throughout the process to ensure alignment of data and valuable assets.
Tagmata Security Assessment Services includes:
- Risk Assessment and GAP Analysis
- Vulnerability Assessments
- Penetration Testing
- RedTeam Operations
- Application/Web/Mobile Testing


Crisis Management & Incident Response (CMIR)
“We don’t rise to the level of our expectations, we fall to the level of our preparation and training.” – Archilochos
The Information Security and Cyber Risk Assessment provides an executive recommendation of strategies and options for a roadmap to address gaps, allocate resources, and improve the efficacy of your security activities. Tagmata advises you on how to protect your organization from the increasing threat landscape by evaluating and making recommendations on the following requirements: Foundational organizational, business alignment, metric and maturity, Risk tolerance, established information security policy, acceptable use policy, information handling policy, password policy, application policy, and mobile device policy.
As your brand becomes more dependent on IT innovation protecting critical information is paramount to reducing your risk and increasing your opportunity for cybersecurity success.
CMIR Preparations Programs Include:
- Executive Report
- Response playbook to leverage during a cyber incident
- Manage Communications
- Retain and Regain Customer Trust
- Restore Digital Process
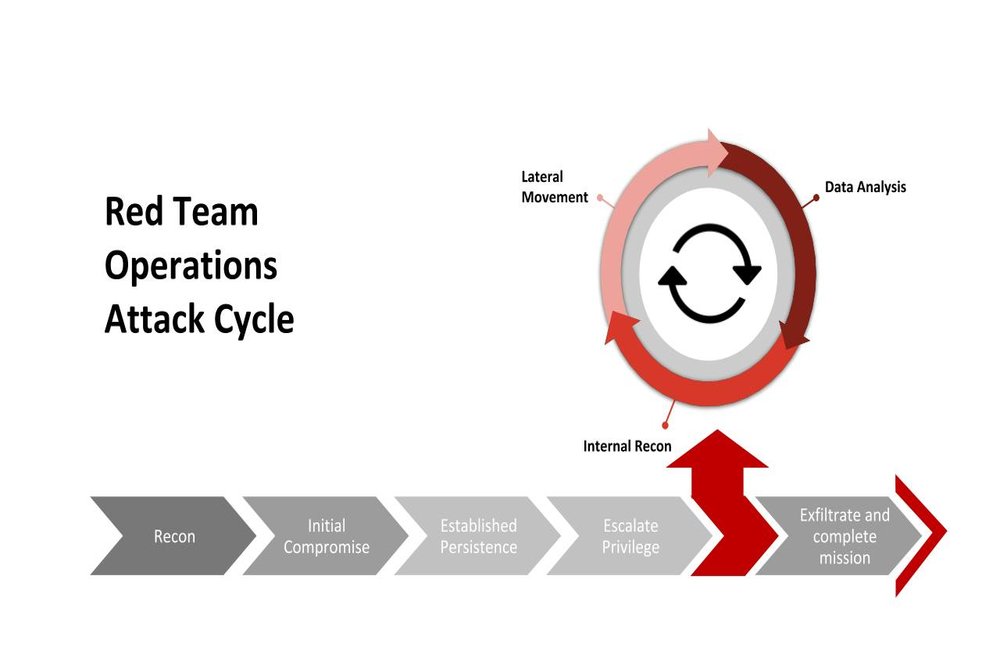
Red Team Operations
Red Team & Blue Team “Real-World” Simulation, Testing, Education, and Operations.
Red Team Services is an official educational methodology offered by the University of Foreign Military and Cultural Studies which is utilized by most branches of the Federal Governments CyberSecurity Teams to prepare, test, practice, remediate and analyze malicious attacks.
Red Team Operations integrates these certified practices into a service program guiding both Cyber and physical security methodologies.
Tagmata RedOps is the De Facto standard for Next-Generation Risk Preparedness, Awareness, and Response:
- Incident Modeling and Counter Manuever Engagements
- Capability Exercise for Cyber and Physical Tactics, Techniques and Procedures (TTPs)
- Assess Readiness and Response Protocols during Major Events
- Physical and Technical Maneuvers for Rapid Response
- Improved Framework for Remediation and Reconnaissance Training

Security Training and Education
Tagmata Education and Technical Training courses are focused on partners and customers. Tagmata EDU provides enhanced cyber "real-world" education and training that vendors and other programs don't offer.
Tagmata develops a custom curriculum which enables our customers to optimize the value and capabilities of their security systems and procedures. Tagmata offers Cybersecurity awareness training, which is essential to reduce the risk that sophisticated phishing or social engineering methods can trick your employees into serving unknowingly as entry points into your information and data systems.
Tagmata Security Awareness programs provide an extensive set of security awareness services:
- Security Awareness
- RedTeam Training
- CMIR Workshops
- PenTest Training
- GRC or Compliance Workshops

